Since the announcement of the COVID-19 pandemic, many companies are trying to stop the spread of the coronavirus by having their employees work from home, including big corporations like Apple and Microsoft.
Switching over can be a difficult transition but working remotely has been shown to be better for your health, for the environment, and–if done right–for your productivity.
This article will discuss keeping up with deadlines, increasing morale, and using the best digital tools to communicate with your team.
A Beginners Guide:

This new pandemic may cause a lot of havoc in your workplace–especially if you’ve never had to manage remote employees. The most important thing you can do is give your staff access to…
- Basic Tools: Working remotely means you need to have these basic tools on hand. Headphones are important to cancel out background noises so your team can focus on their tasks. Webcams are needed so your team can have virtual meetings. And most importantly, a strong wifi connection.
- Secure Wifi Connection: Having a secure Wi-Fi network along with a virtual private network, VPN, creates a combination that protects information from being hacked. A VPN takes any transmitted data and encrypts it to protect it from any unwanted users.
- Proper Technology: Picking the proper programs is important because your team needs to communicate. From video-chatting to virtual chat rooms, secure collaboration will keep employees productive. We’ll discuss the best software at the end of the article.
These tools are crucial to a successful remote workplace. But you need more than just tools to keep your team productive.
Deadlines, Deadlines, Deadlines!

Setting expectations early on is necessary for everyone to set their own individual goals. Making clear deadlines and team goals keeps everyone on track.
Expectations should include the following: how long it should take to complete their tasks, how everyone should be communicating, and how often they need to be online. You also need to make sure you have the same expectations for yourself.
In making expectations, hard deadlines need to be your team’s first priority. Whether you’re making daily, weekly, or monthly deadlines, create a list where team members can access their tasks whenever they need to.
Tracking progress will help you to see if employees are struggling with certain tasks. This way, you are able to help out as needed.
Another way to help achieve deadlines is to be mindful of your employees’ individual home lives.
Regular 1-on-1 meetings are a great way to establish a rapport with your team members.
It allows you to check on progress, establish an effective line of communication, and learn about any issues that might affect their work. Learning about these issues will give you insight on how to lead your team.
If you have a student who went back home, they may be in a different time zone. This is important to keep in mind so you’re not scheduling a video conference for 5 a.m.
Keeping Up Morale

A common issue among remote employees is feeling like their work isn’t seen or appreciated. Feeling unappreciated can lead to a lack of motivation.
Kill this problem before it starts by praising team members. It’s a simple way to make sure everyone is feeling included in the team. More importantly, it keeps morale high.
Allowing for flexibility is another great way to increase morale. Flexible hours gives each individual control in their routines and allows them to complete a task in a way that is best for them.
Offer Collaboration

With anything in life, there will always be downfalls. Sometimes it can be hard to see common problems when the entire team is working from home.
By offering a way for individuals to express their concerns, you can fix these issues before they snowball into something bigger.
The best way to hear these issues is by offering a pressure free environment where employees can trust that they’re being heard.
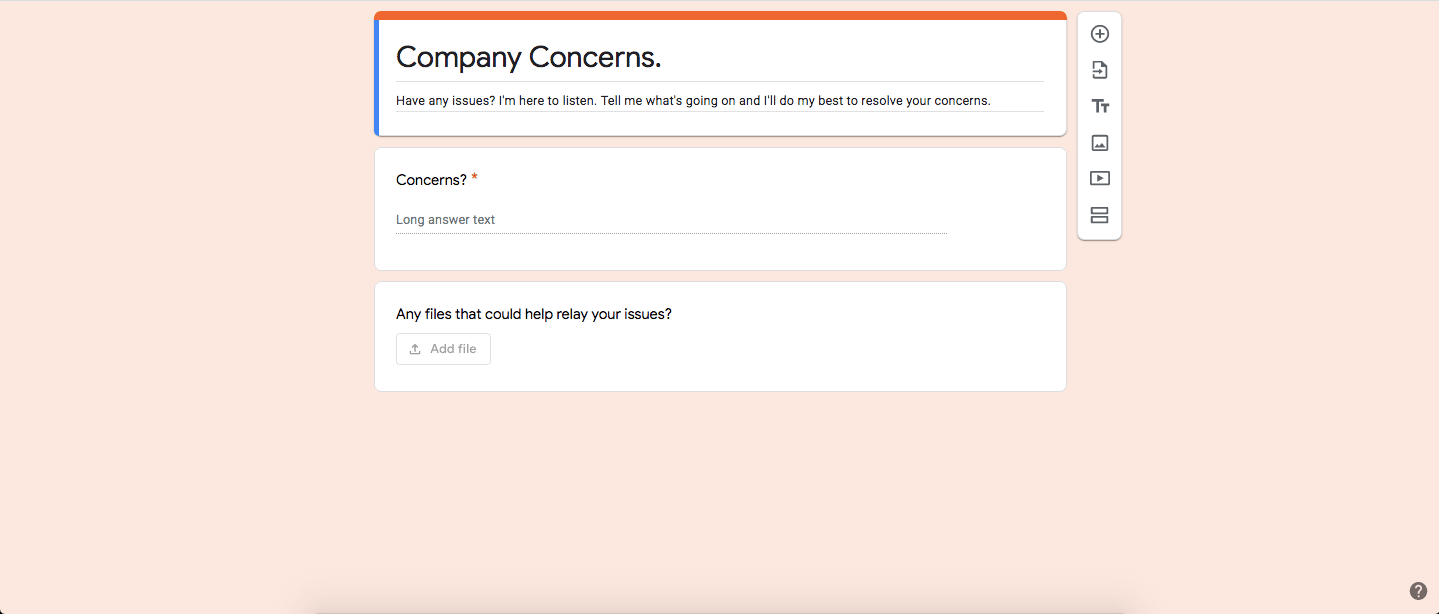
By using Google Forms, I’ve created an anonymous outlet where company members can type their concerns and attach relevant files if necessary.
Oftentimes, concerns will come if expectations aren’t clearly established. Not only should you have goals for everyone as a whole, but you should encourage everyone to set individual goals for themselves.
Ask around for personal goals and make sure you’re keeping track of them. By doing so, you as a boss can find ways to help your team to achieve their goals.
Having a buddy-system is another way to make sure everyone is meeting their goals. By pairing everyone up, your team has a few individuals they know they can rely on if they need help or are lost in a task.
These 1-on-1 checkups also establish better lines of communication through employees.
Which Tools are the Best for my Workplace?

Communication is an important part of every relationship. This includes the workplace.
By having different tools for effective communication, this makes it easier to work remotely.
For video conferencing, I recommend Zoom. Zoom is great because you can conference 1:1 or with 100 others (depending on which plan you pick, you even have up to 1,000 video participants and 10,000 viewers).

Zoom offers flexibility in being able to securely access it from your mobile or desktop device. You can also record your meetings and they’ll transcribe themselves.
Big companies like Uber, Go Daddy, Pandora, Dropbox, and more are already using Zoom.
This program also offers a “chat” section where members can communicate individually, in groups, or with clients.
Although Zoom is great for video-chatting, I recommend Slack for messaging.
Through Slack, you can create different channels for different needs and communicate directly with anyone.
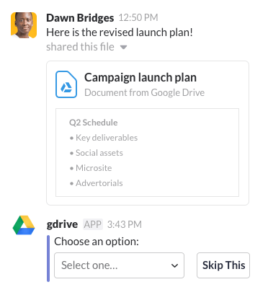
One of Slack’s best features is that it integrates programs you likely use every day. These programs include Dropbox, Asana, and all google applications.
Slack also allows you to search, which is helpful when you know a file has been sent to you but you can’t remember where it was sent.

With Zoom for video conferencing, Slack for messaging, there’s one tool missing for what you need: Project tracking.
Fyresite, along with over 150,000 businesses, uses Zoho because of its many functions. With Zoho, you can clock in and out, log how much time you spent on a particular task, write notes about the tasks you’re working on, and much more.
It also allows you to connect with your customers, which makes it easy for them to check on your progress.
A Healthy Team is a Happy Team
As an employer, keeping your team healthy and happy should be a priority–especially during a public health crisis.
By allowing your team to work remotely, this will insure that your company is still running efficiently while your team members are safe from viruses.
Was this article helpful? Reach out online and let us know, or call us if you have any questions about how your team should integrate.
 Lauren Lively
Lauren Lively 

