It’s about time we got a CEO’s guide to blockchain.
Blockchain is not just for cryptocurrency. In fact, many CEOs will be using blockchain within a few years (if not already).
After the blockchain market shot up to $3.67 billion during the COVID-19 pandemic, Grand View Research predicted an 80% growth by 2028.
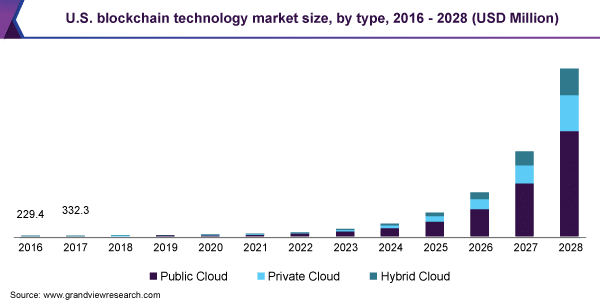
That’s huge.
In fact, even the most vocal crypto skeptics acknowledge that smart contracts and blockchain middleware hold promise in the business world.
Thus, there’s no doubt that blockchain will be part of every CEO’s future.
You WILL use blockchain by 2028 if . . .
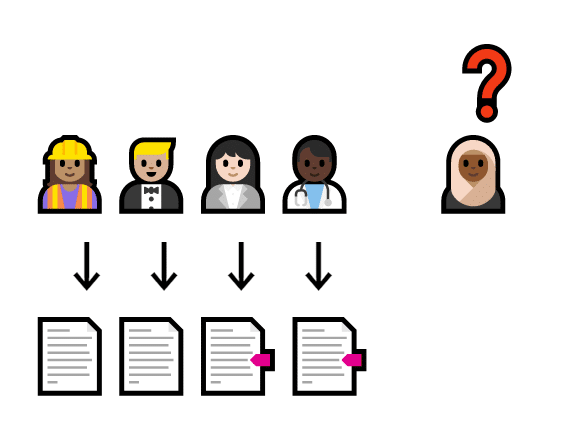
- your company belongs to the finance, healthcare, technology, insurance, or supply chain industries
- IT infrastructure within your company relies on a private cloud
- supply chains are a vital part of your business
- global transactions occur regularly
There’s just one problem: most of the blockchain guides aren’t too great. They usually have a few major problems.
- Many blockchain guides are written for engineers, not CEOs. You don’t need linear algebra to understand how blockchain works.
- Alternatively, they’re written for casual enthusiasts, not CEOs. If your business may use blockchain soon, you’ll need a deeper understanding.
- They’re bitcoin-focused, not blockchain-focused. Unless you accept pay in bitcoin, you’ll probably not use cryptocurrency any time soon. Blockchain isn’t bitcoin.
- Finally, they’re rarely built for visual learners. Sure, you’ll have a couple of graphics sprinkled in, but that’s about it.
We set out to solve all of these problems in a super special blockchain guide for CEOs (and other business pros).
- It teaches in concepts, not formulas
- It goes deeper than those “it’s just a decentralized database” guides
- The ledger keeps track of trades, not money
- Each major step comes with an illustration
Buckle up! Blockchain’s coming, and this guide will have your business team prepared.
Oh, and if you’re already building a crypto project, check out these crypto website design trends and examples, too.
In one sentence . . .
Blockchain is a big, untamperable list of trades spread across lots of computers.
If you’re just trading cryptocurrencies or NFTs, that’s about all you need to know. But if you’re leading any project related to blockchain, it helps to know how the whole thing works.
We’ll keep everything high-level and easy to understand, then list some resources with more information.
CEO’s Guide to Blockchain Part 1: Trades
Since Blockchain is a list of trades, we need something to exchange. It could be money, data, or really anything that could be digitized.
In our example, an artist makes her own cat trading cards.
An artist creating a cat
She and her friends trade and collect the cats all the time. But when the pandemic hit, trading got a little trickier.
How can she keep these cat trades going?
CEO’s Guide to Blockchain Part 2: Ledger of Trades
To keep trading going, the artist makes a shared spreadsheet. Every time someone wants to trade a cat, it goes on the sheet.
A ledger of cat trades. Each list item contains an illustration of people exchanging cats
Once everyone meets up in person again, she’ll go through the spreadsheet and figure out who gets which cat.
The artist is looking at a sheet and giving people cats based on what the sheet says
Thus, a trade written on the spreadsheet is as good as an in-person trade.
But this system isn’t perfect because there’s no way to check if a trade is real. Carina could write that Barry gives her a cat, even though Barry never agreed to the trade.
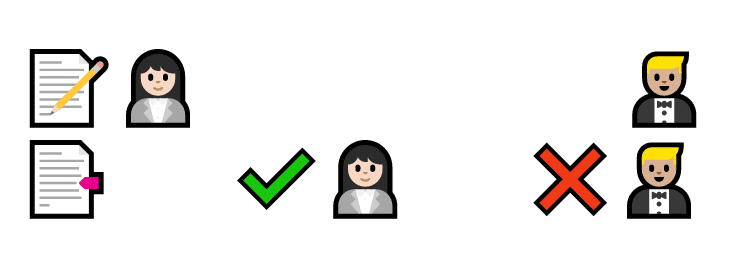
First, Carina writes that Barry owes her a cat. She says it’s true, but Barry says it isn’t
If the artist wants this system to be trustworthy, she needs digital signatures. But squiggles can be copied and pasted. She needs a better system to sign off on cats.
CEO’s Guide to Blockchain Part 3: Signatures
Verifying a trade digitally requires some careful math. The artist thinks about it and comes up with a plan.
First, she assigns everyone a private key. The private key is a very large prime number that sort of works like a secret ID number.
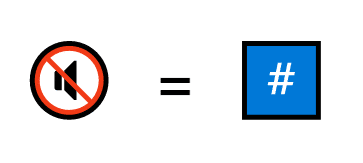
A private key is (at its core) a prime number
Then, she makes a program that inputs a cat trade and outputs a seemingly random prime number.
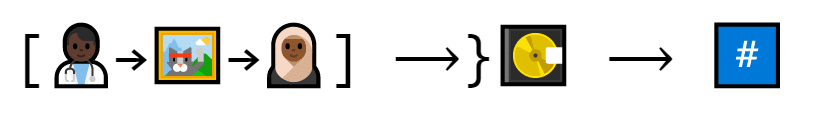
A program looks at Dion and Ellen’s cat trade and generates a seemingly-random number
There’s a secret system, but if even a tiny thing changes, the prime number looks completely different.
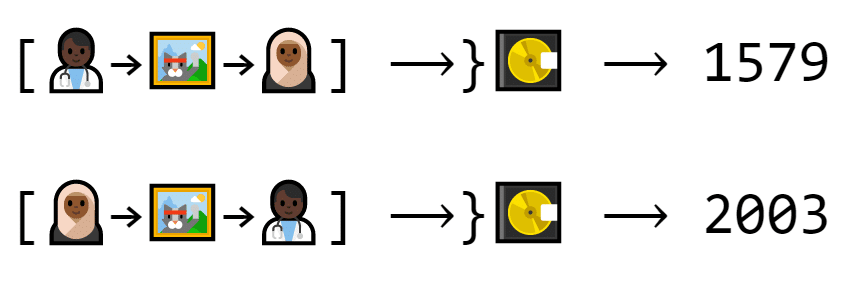
Trade 1 produces the number 1579. Trade 2 produces the number 2003. The trades are the same, but in a different order. This significantly changes the output.
The idea is that any time someone wanted to trade cats, they multiply their private key and their cat number together.
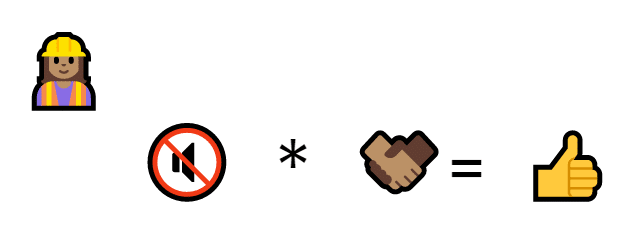
Al multiplies the private key number by the number that the program generated to get a signature
Like a signature, a product of primes is really easy to make (you just multiply the two numbers together) and very hard to fake.
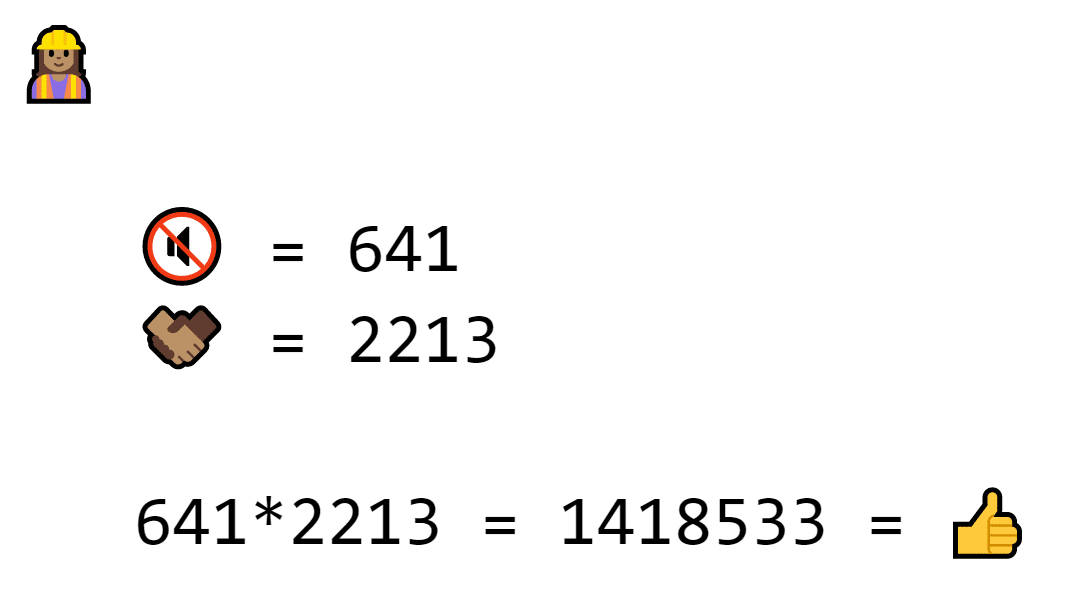
The variables are replaced with numbers. Private key is 641 and exchange number is 2213. 641 * 2213 = 1418533, which is the signature
In fact, your best bet for faking a product of primes is to guess and check, and once the primes get big enough, it gets really tricky.
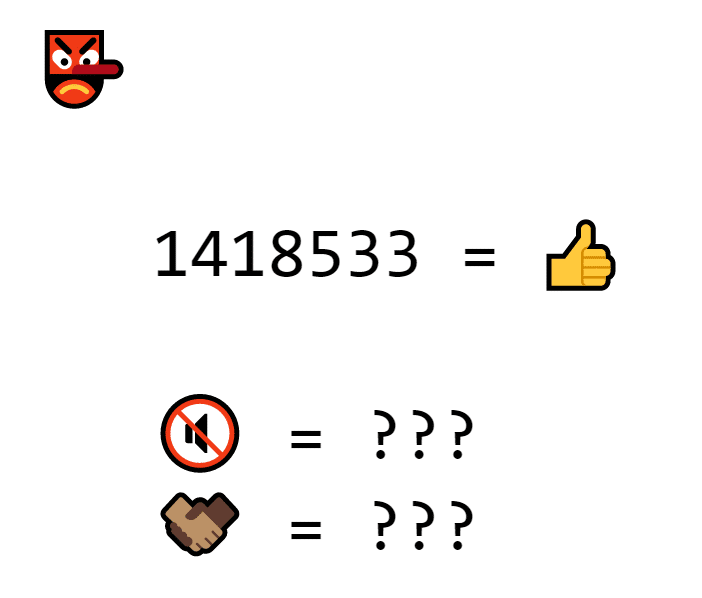
The hacker knows that 1418533 is the signature, but can’t figure out the factors
Even a computer can’t do it once the primes get really big. Bitcoin’s cryptography parameters include the prime 2256 – 232 – 29 – 28 – 27 – 26 – 24 – 2 — it’d take far too long for any computer to find the factors of primes this big.
There’s only one problem: since the cat number changes every transaction, you can’t verify signatures by comparing them side-by-side.
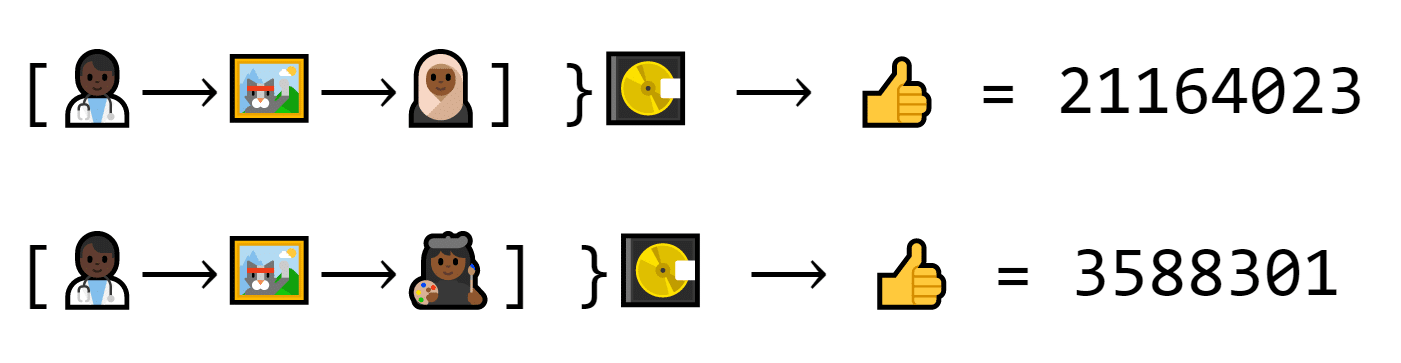
Dion makes two trades. The first one makes the number 21164023. The second one makes the number 3588301. Both are real trades, but neither look the same.
But the artist thought ahead. Everyone also received a unique public key.
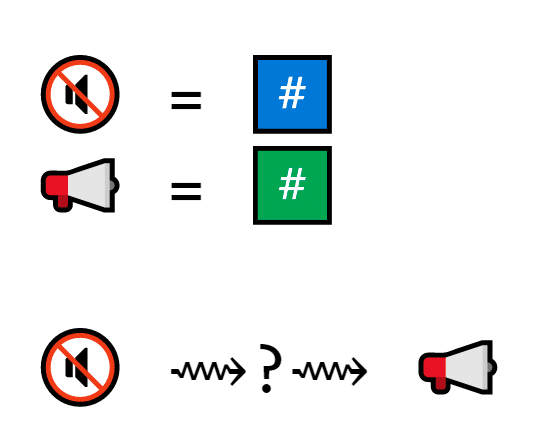
The public key is also a number. It’s related to the private key, but not in an obvious way.
(We will be using prime numbers as examples, but the public key
The public key is the private key’s outgoing cousin: it’s not the same thing, but it shares some DNA.
If you pop the public key into a program with a cat trade and its signature, the program can confirm if the signature is real or not.
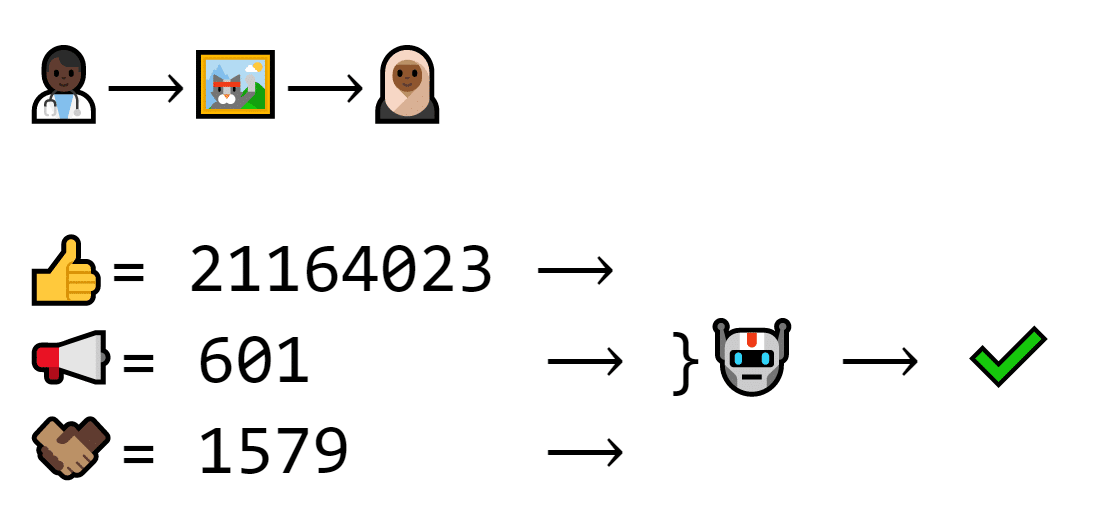
A different program looks at the signature (21164023), the public key (602) and the exchange number (1579) and verifies that it’s a real transaction
The math is really complicated, but in a nutshell, the program checks two things:
- if the signature was made using this cat trade
- if the signature was also made using a number “made from the same stuff” as the public key
That way, the program can identify if the private key is the same without actually knowing the private key.
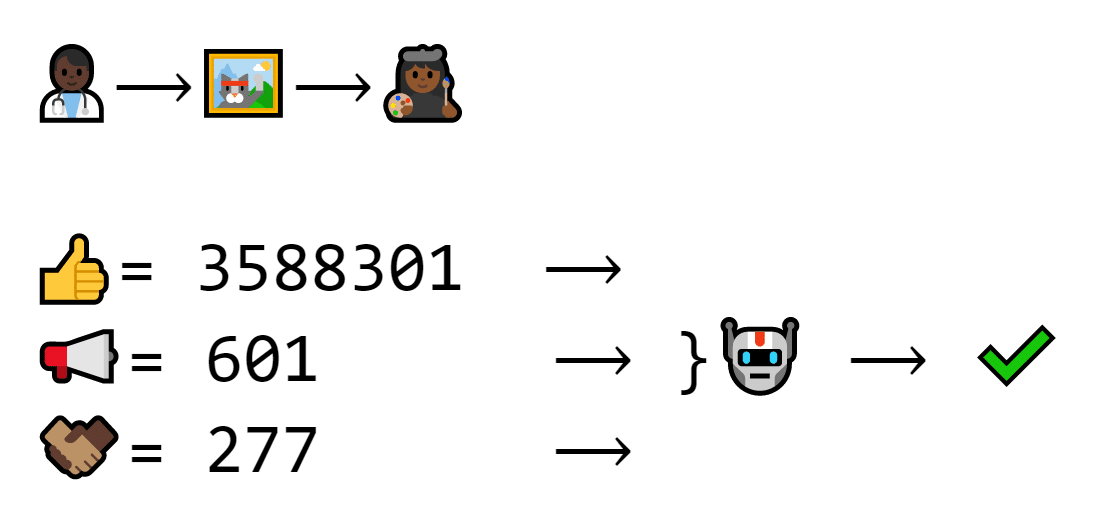
This transaction has a different recipient. Thus, the signature and exchange number are different, but the public key is the same. The machine still verifies
Since the public key is related to the private key in a super-secret way, the program can tell if the right private key was used, even if the signature looks different each time.
But if a signature wasn’t made with the right private key, it won’t work.
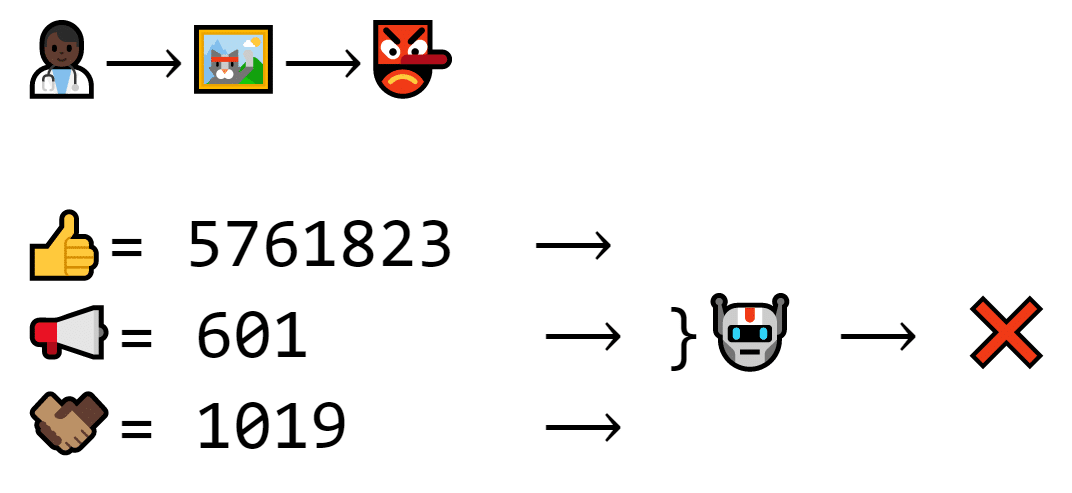
The recipient is a hacker this time. The hacker didn’t use the right private key to make the signature, so even though the machine doesn’t have the private key, it knows it’s wrong.
So far, the traders have progressed from trades to a list of trades to a signed list of trades. If the artist is a fair person, this is enough.
But if the artist were a dishonest person, none of these security measures would make a difference.
CEO’s Guide to Blockchain Part 4: Centralization Problems
The current cat trading spreadsheet is a centralized database (in the simplest terms, a database is basically just a box of digital spreadsheets). It’s centralized because the entire cat economy goes through a single central point.
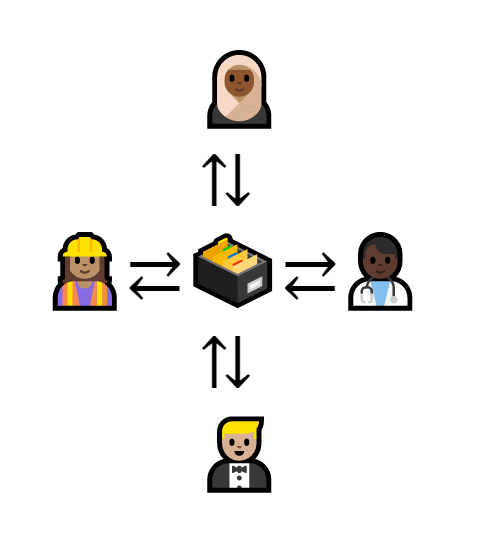
Four people connect to a central database
A centralized database can be nice. If someone makes a new trade, you only have to write it down in one place.
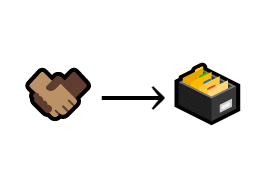
A new trade is written down in the database
But a centralized system isn’t always very secure. If the database explodes in a freak accident, the entire cat economy goes away.
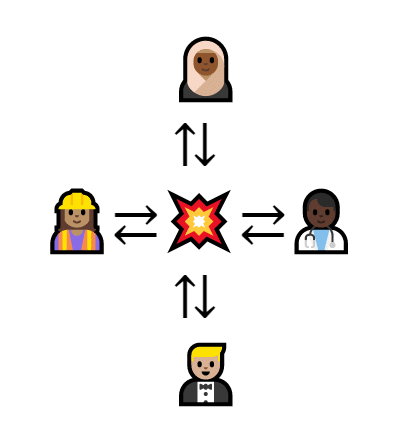
The database breaks, so the network collapses. No one can trade without the center
Backups aren’t enough to fix everything, either. That’s because centralized databases create a single point of control.
If the artist decided to lie that Dion owes her a cat, nobody could prove her wrong.
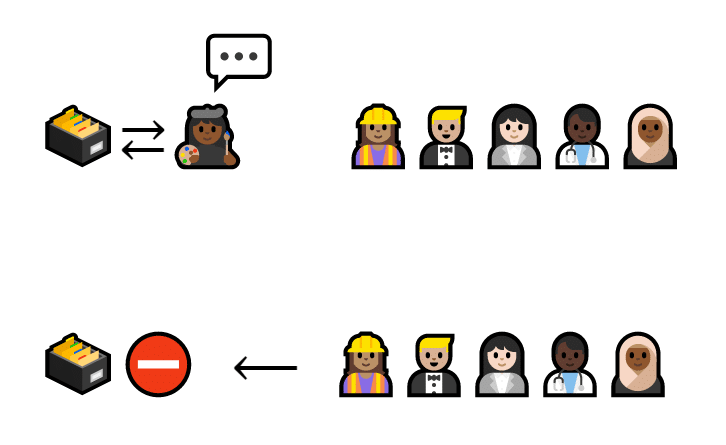
The artist says that Dion owes her a cat. She’s the only one connected to the database, so no one else can check.
To make the cat trades more transparent, the artist needs to decentralize.
CEO’s Guide to Blockchain Part 4: Basic Decentralization
To put the power in the hands of the traders, the artist decides to use a decentralized system. Instead of making all trades go through a single spreadsheet, everyone has their own copy.
Everyone is connected to their own list
Whenever a trade takes place, the traders announce it in a group chat. Everyone checks the signature and adds it to their own copy of the list.
Everyone records a transaction between Al and Barry
This system is completely disaster-proof. If Dion’s computer breaks down, everyone else has a copy of the data, and trades keep going.
Everyone updates their list with a new transaction. Dion’s list explodes, but since everyone else has a copy, the trading continues
Best of all, the artist can’t lie about what’s on the sheet. Everyone has their own copy, so everyone knows how much everyone else owes.
The artist lies about her sheet, but everyone has their own copy and corrects her.
However, there’s one very big problem. There’s no guarantee that every list looks the same.
If enough people forget to list a transaction, it didn’t happen. So if Al, Barry, and Carina dislike Dion, they can decide to ignore that he received a cat from Ellen.
An equal number of people ignore and record a transaction
Then, because it’s not on the lists, it didn’t happen.
To solve this problem, we need to create a self-referencing system. That way, if a transaction gets left out, the list isn’t valid.
But how do we do that?
CEO’s Guide to Blockchain Part 5: Basic Blockchain
Let’s start by putting each trade (or a group of trades) into a box.
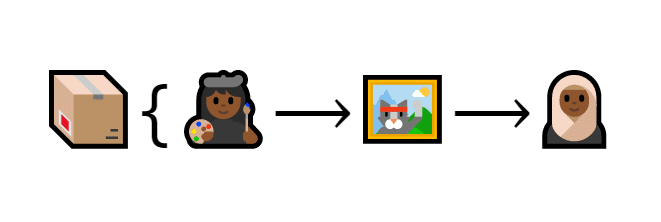
A transaction is put inside a box
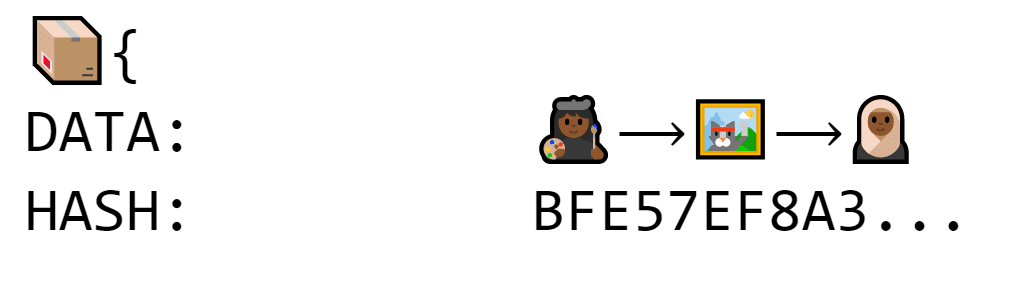
This box is called a block. Each block is also identified by something called a hash. It’s basically a big string of seemingly random data.
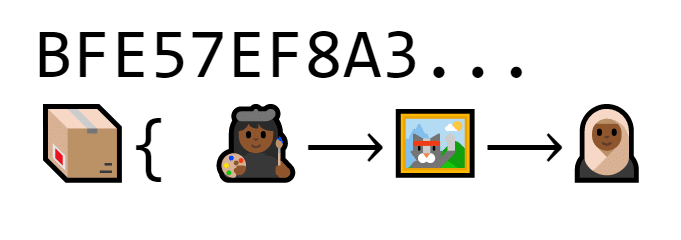
The block is “labeled” with a long string of characters (BFE57EF8A3…)
If anything inside the block changes even a tiny bit, the hash changes completely.

A hacker makes himself the recipient of the cat, but the hash changes
When we add a second block, it has a unique hash, too.
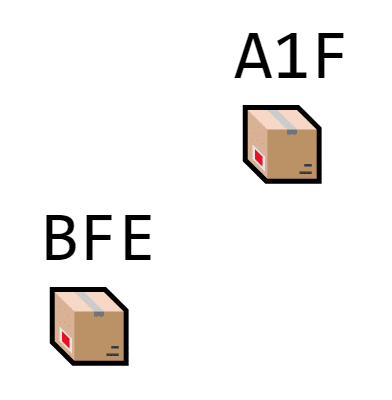
THIS block’s hash begins with A1F
The second block needs to somehow show that it’s second on the list. That’s why the second block also contains the hash of the block right before it.
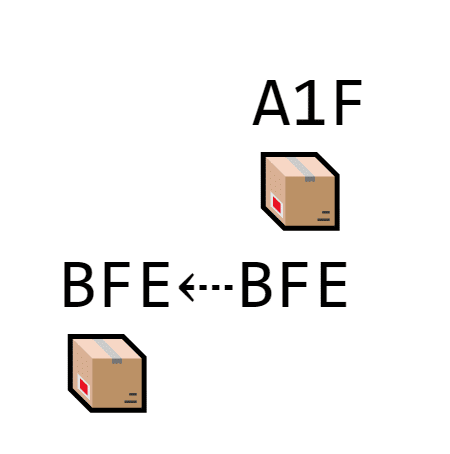
The second block includes the hash of the block in front of it
Every time a new block gets added to the chain, it must contain the hash of the block right in front of it.
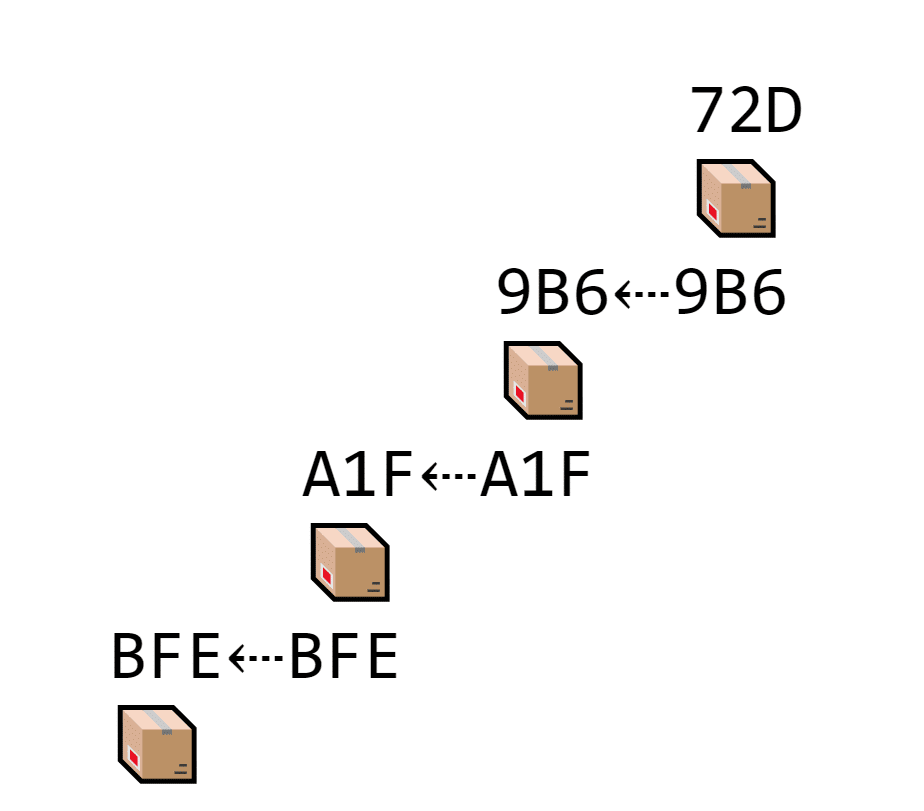
EVERY block stores its own hash and the hash of the block in front of it, which makes a long chain of transactions
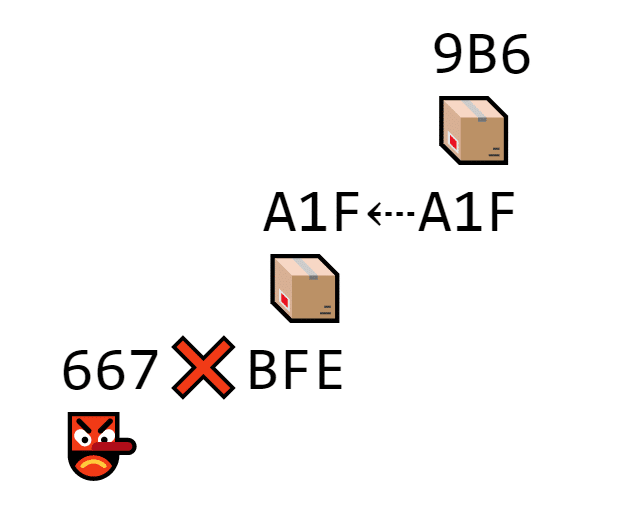
That way, if Carina forgets a block, she can’t add any more blocks to her list.
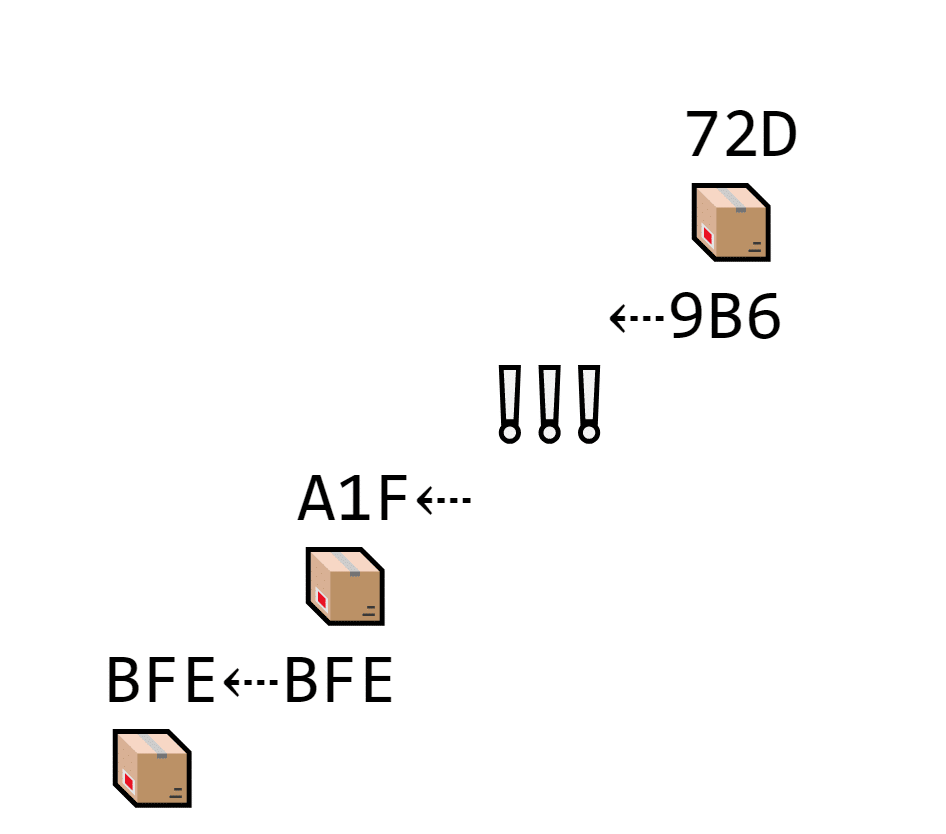
Carina forgets block 9B6. The next block contains its own hash (72D) and the previous hash (9B6). But there isn’t a block with 9B6 on the chain, so it doesn’t connect until Carina adds 9B6 back.
This type of list is called a blockchain because it’s, well, a chain of blocks.
(It’s about time we got to blockchain in the CEO’s Guide to Blockchain).
Because each block references the one before it, the whole blockchain is very hard to edit. If a hacker wants to change a transaction earlier on the list, the hash changes and no longer matches the following block.
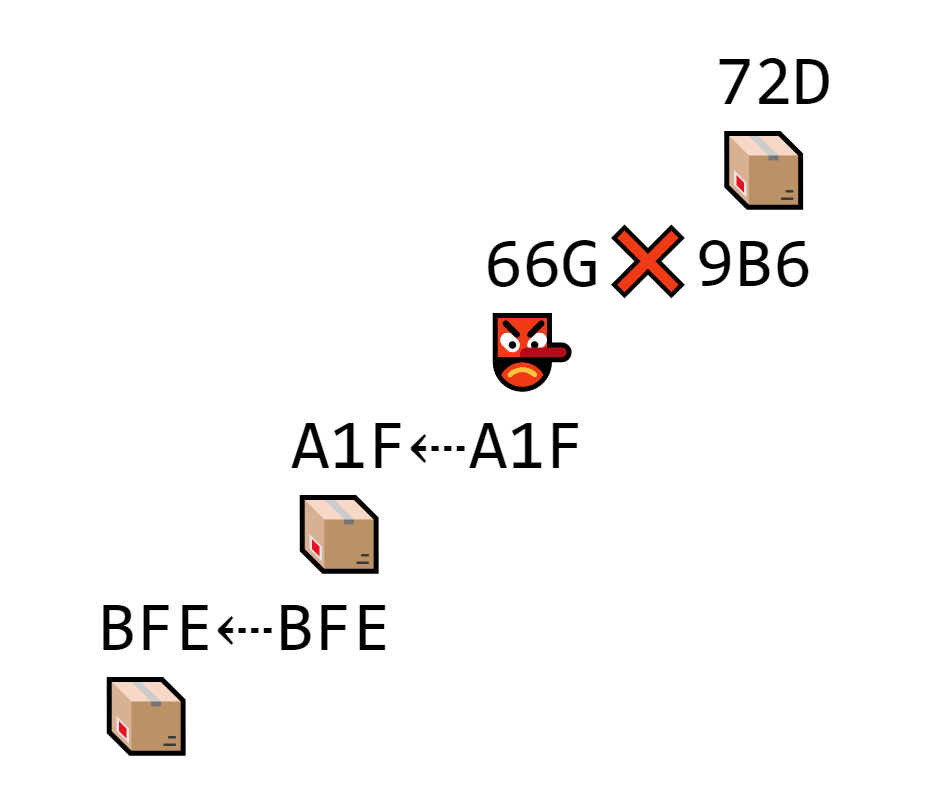
The hacker edits the data inside block 9B6. Because the data changes, so does the hash, and it no longer matches the next block.
The only way to hack a block is to hack every single block that follows it and every block to follow.
But what if Al and Barry have one blockchain, but Carina and Dion have another? How does Ellen know which one is right?
Two people have one list, but two people have another conflicting list. Which is right?
There are a number of ways to achieve consensus. These methods are called consensus algorithms since they achieve consensus.
The original bitcoin paper introduced Proof of Work, but we will also discuss a popular alternative called Proof of Stake.
Proof of Work
The super simplified idea behind proof of work is that the longest blockchain is real because it took the most work to make (and, thus, would take the most work to hack).
As-is, these blocks don’t take a lot of work to hack. Since they’re basically just data and a hash, a hacker can change it pretty quickly.
The block is just a trade and a hash. It shouldn’t take long to hack or edit
Of course, it won’t match the following block, since it stores the valid hash. Crisis averted, right?
The hacker successfully changed the first block, but not the second block, so the hashes don’t match
Not exactly…
Since blocks don’t take long to hack, a hacker could hack every item on the list.
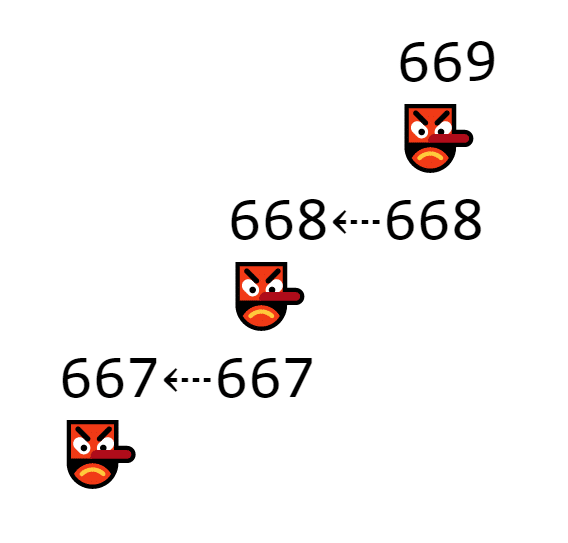
Because the hacker edits every block on the list, all the hashes match
To prevent this from happening, Proof of Work makes blocks more time-consuming to change using mathematical puzzles.
In order for a block to be valid, it must include evidence that a lot of work was spent, or a proof of work.
In this case, each block must include a number that makes the hash pop out with five zeroes at the beginning.
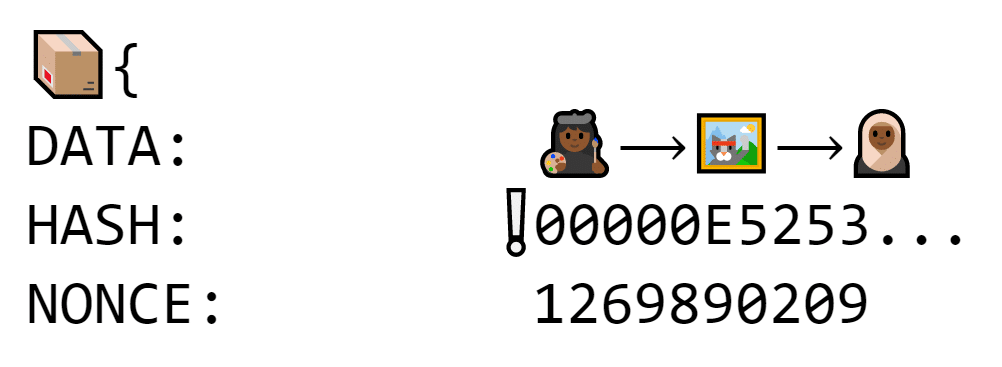
If adding data makes the hash change, people can test random numbers until one makes the hash start with a bunch of zeroes
The nonce requires a lot of work to figure out. Because a tiny change in the data makes the hash look completely different, the nonce could be 2 just as easily as it could be 2,578,129,982.
The only way to find it is to guess and check until something works. If the nonce is off by even one the hash looks completely different.

If you add one to that number, the hash completely changes
But if Al plugs in the nonce that makes the hash start with five zeroes, anybody can verify instantly by looking at the hash.
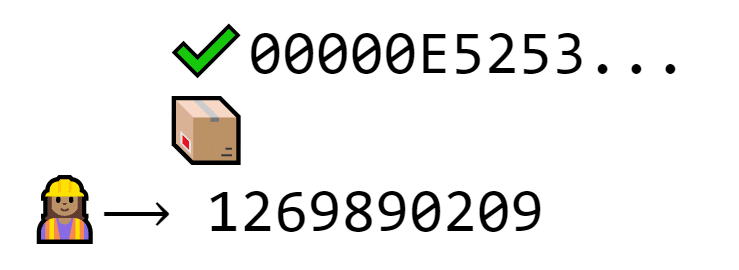
Those zeroes prove that Al did the work without making others do the work themselves
Any user that verifies a block is called a miner. Since this process takes so much time and work, miners get rewarded with a free cat.

Al is rewarded for proving her work with a free cat generated from thin air
You don’t have to be a miner to use the blockchain. Al and Barry may mine, but Carina, Dion, and Eshal just need to keep their own lists up to date. Traders trade; miners verify.
In case this is a bit confusing, here’s a simple flowchart.
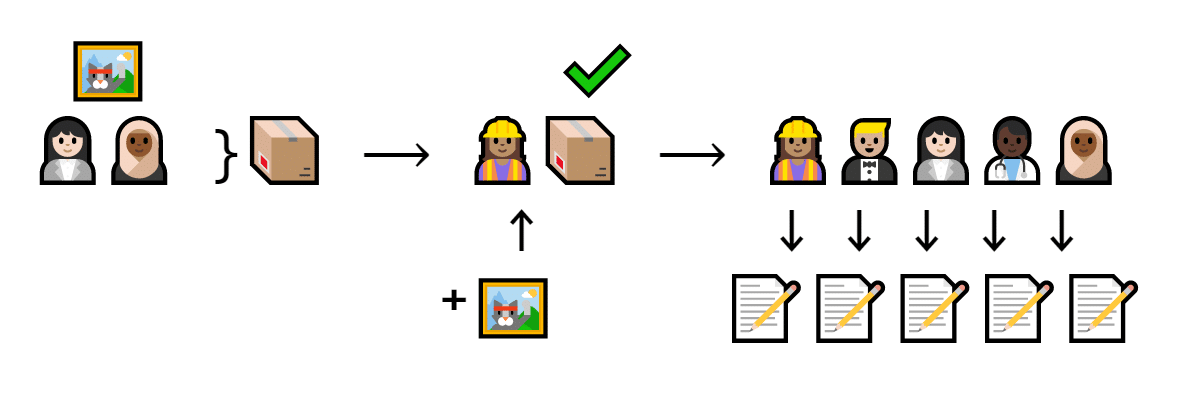
Carina gives Ellen a cat. This transaction fits in a block. Al verifies the block and gets a free cat. Everyone writes it down on their own list.
Carina and Ellen trade a cat. That trade goes into a block. Al the miner verifies it and tries nonces until the hash starts with five zeroes. Once she finds one, everyone updates their copy of the list.
See why this works? It takes so much work to make a block that a hacker can’t possibly hack the entire blockchain.
Let’s say it takes ten minutes (like Bitcoin) to find a nonce that makes the hash start with zeroes. A hacker spends ten minutes hacking one block, then starts hacking the next one to make the hashes match.
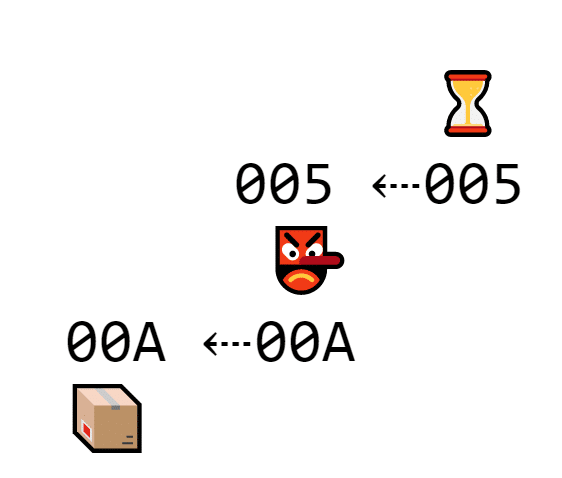
A hacker is spending time trying to hack a second block
But at the same time, multiple miners are verifying blocks. For every block the hacker fakes, three miners can validate three blocks.
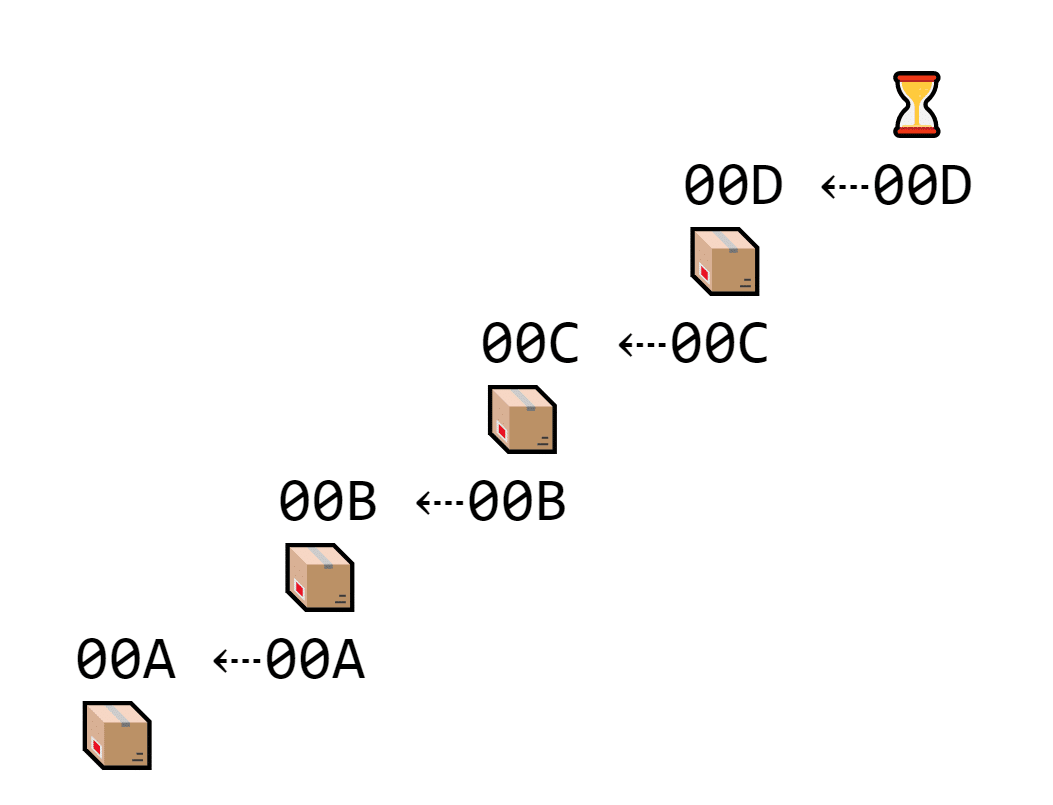
In the time it takes one hacker to edit one block, several miners verify a ton more blocks
Thus, the longest chain took the most work to make, so everyone defaults to it and the fraudulent chain gets ignored.
To hack the blockchain, the hacker needs to verify transactions faster than the entire network.
But proof of work isn’t flawless. It takes so much work to mine that miners need massive computers and tons of electricity to make it worthwhile.
The miners benefit from the economy of scale and generate lots of cats for their own hoards while destroying the environment with massive electricity usage.
That’s why Proof of Stake entered as an alternative.
Proof of Stake
While Proof of Work requires miners to prove that it’d be harder to fake it than to make it, Proof of Stake requires verifiers to prove that they’d lose more money by faking than by making it.
Instead of miners, Proof of Stake uses validators.
To become a validator, a cat trader gives some of their cats to the network deposit.
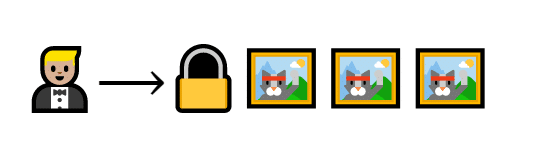
Barry puts three cats in a locked box
These cats are called a stake, and they work sort of like collateral. If a validator verifies a fake transaction, they lose part of the stake.
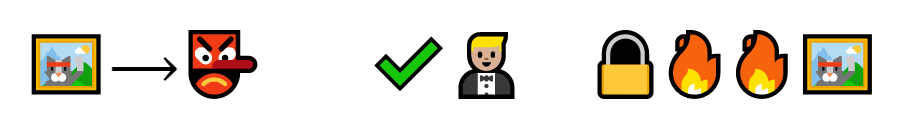
Barry verifies a fake transaction. Because it’s fake (maybe it has no signature), Barry loses two cats
But if they do it correctly, they get rewarded with transaction fees.
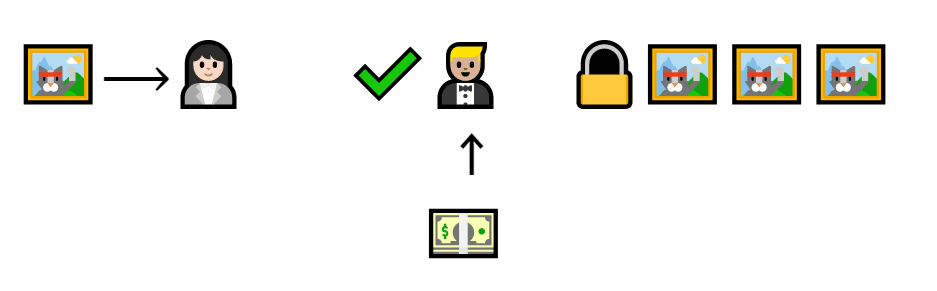
Barry gets paid for verifying a real transaction
This system does not work if the stake is smaller than the transaction. The validator could just verify fake transactions that give them more cats than they lose.
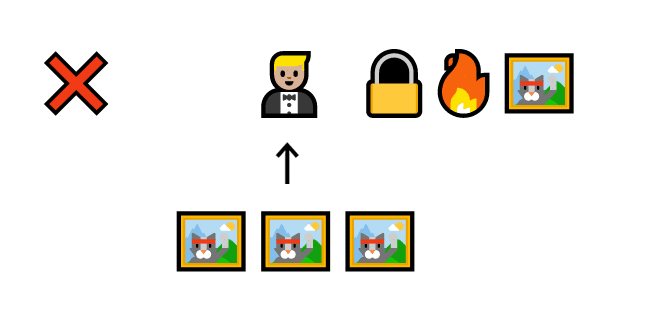
Barry loses one cat, but gains three by verifying a fake transaction
Instead, validators must always have more cats on the line than they could get from cheating the system.
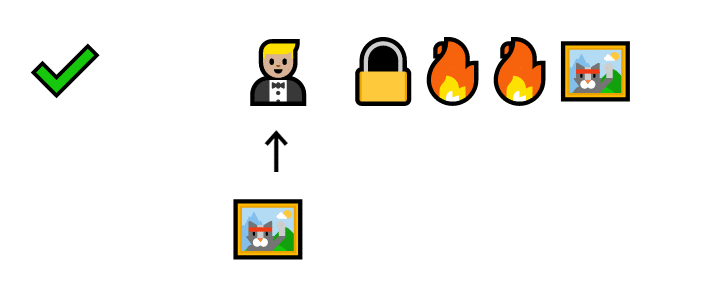
Barry gains a cat by verifying a fake transaction, but loses two cats
If the validator has a bigger stake on the line, they can be trusted even more. If Dion would lose four cats and Barry would only lose two, Dion would be much less likely to verify an unsigned or fraudulent transaction.
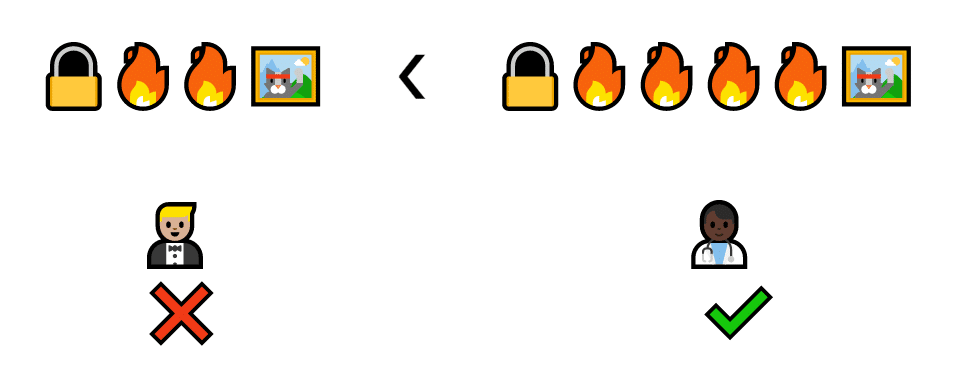
Dion loses four cats every time he verifies a fake transaction (because he has more cats) so he will be less likely to lie.
For this reason, whenever the system needs to choose someone to validate a transaction, it favors the people with more cats in that deposit.
Proof of Stake is very popular because it verifies transactions up to five times faster, uses much less energy, and even keeps transaction fees lower (since the fees don’t have to support expensive mining). It also serves as the foundation for other consensus algorithms, such as delegated and leased proof of stake.
Whether the traders use Proof of Work, Proof of Stake, or some other method, they can be sure that the blockchain system is extremely secure.
More resources
At this point, the traders have developed a reliable way to exchange and track digital cats without keeping all the power at the center. It’s extremely hard to tamper with and full of security measures. Once a cat trade ends up on the blockchain, it’s very likely there for good.
However, this CEO’s guide to blockchain only scratches the surface of all this complex math, code, and engineering. That’s why we’ve listed amazing resources to help you along your crypto journey.
Explore Tools
- The Sha256 Hash Generator lets you plug in any text to generate a unique hash. It’s great for demonstrating just how seemingly random those hashes are.
- Blockchain explorer lets you browse individual blocks on the bitcoin, bitcoin cash, and ethereum networks.
- To get an idea of what dApps are out there, the Graph is an awesome starting place.
Read guides
- IBM, one of the biggest players in private cloud blockchain solutions, produced a great blockchain for dummies ebook.
- The IBM Blockchain for Business page has lots of great resources and guides, too.
- Rider University has a great article and infographic about blockchain for business. It’s not as in-depth, but it’s pretty.
Watch videos
- 3Blue1Brown’s video on how bitcoin works is absolutely brilliant. It inspired much of this guide and dives a bit deeper into math and encryption.
- Similarly, the 3Blue1Brown video on 256 bit security visualizes just how impossibly hard it is to “guess and check” your way through those signatures.
- For a more mathematical perspective, check out Stand-up Maths’ video on open mathematical secrets. He makes the math behind the Shamir Secret Sharing System extremely approachable and fun.
- Perhaps the best resource for video-based learning is Brilliant.org (this is not sponsored). This series on Blockchain fundamentals is superb.
Get Certified
- The Brilliant.org course on cryptocurrency is great for a deeper, yet understandable dive into the cryptography side of blockchain. It’s focused on cryptocurrency more than blockchain, but it’s still a great resource
- Udemy’s Blockchain A-Z course costs $139.99 and gives you lots of resources, downloadables, and more. Upon completion, you get a free certificate.
- Coursera’s highly-reviewed Intro to Blockchain gives you tons of tangible tips and a free LinkedIn Certificate.
- For a more formal training, use Edureka’s blockchain certification training. It costs $399, but has over 20,000 5-star reviews. Experience with object-oriented programming is required.